 The most by and large saw kinds of malware solidify infections, keyloggers, worms, Trojans, ransomware/crypto-malware, thinking bombs, bots/botnets, adware and spyware, and rootkits. You can decrease or reduce malware assaults by brainstorming security frameworks, doing security care arranging, utilizing an application-based complex check, familiarizing disagreeable malware and spam channels, changing default working construction moves close, planning standard inadequacy assessments, or can stop. For More information visit TechKorr.
The most by and large saw kinds of malware solidify infections, keyloggers, worms, Trojans, ransomware/crypto-malware, thinking bombs, bots/botnets, adware and spyware, and rootkits. You can decrease or reduce malware assaults by brainstorming security frameworks, doing security care arranging, utilizing an application-based complex check, familiarizing disagreeable malware and spam channels, changing default working construction moves close, planning standard inadequacy assessments, or can stop. For More information visit TechKorr.
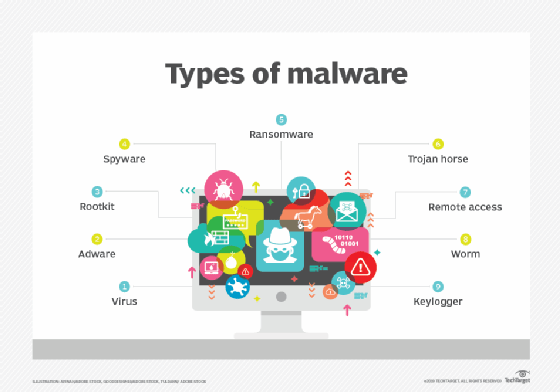
Under, we depict how they work and give certified events for each.
1. Ransomware
Ransomware is a modification that utilizes encryption to hinder an objective’s acceptance to their information until an outcome is paid. The abused association can’t work until decently or completely paid, yet there is no confirmation that part will accomplish the significant unraveling key or that the unscrambling key given will work appropriately.
2. Fileless Malware
Fileless malware presents nothing every step of the way, considering everything, it makes changes to records that are close by to the working framework, like PowerShell or WMI. Since the working framework confides in the changed records to be genuine, a lethargic assault isn’t gotten by antivirus programming – and considering how these assaults are secretive, they are on various events more useful than customary malware assaults. Do you know about another malware called VBS: Malware-gen.
3. Spyware
Spyware gathers data about the exercises of clients without their comprehension or assent.
The utilization of spyware isn’t simply restricted to work area programs: it can work on an enormous application or even on a remote.
4. Adware
Adware tracks a client’s riding improvement to figure out which notification to show to them. Despite the way that adware is like spyware, it presents nothing on the client’s PC, nor does it get keystrokes.
The gamble in adware is the disintegrating of client security – the information got by adware is gotten along with information, either straightforwardly or subtly got, about client action somewhere else on the Internet and used to make that particular profile. Which coordinates their accomplices, what they’ve purchased, where they’ve voyaged, and so on. That data might be shared or proposed to promote experts without the assent of the client.
5. Trojan
A Trojan covers itself as helpful code or programming. Now when downloaded by puzzled clients, the Trojan can anticipate command over misfortunes’ designs for malicious purposes. Trojans can stow away in games, applications, or regardless, programming patches, or they can be implanted in affiliations related to phishing messages.
6. Bugs
Worms target weaknesses in working designs to set out a strong basis for themselves in networks. They can get entrance in various ways: through underhanded permission to the thing, through unplanned programming deficiencies, or through a burst drive. Once introduced, worms can be utilized by harmful entertainers to send off DDoS assaults, take fragile information, or perform ransomware assaults.
7. Pollution
Pollution is a piece of code that inserts itself into an application and is executed when the application is running. Once inside the affiliation, pollution can be utilized to take delicate information, transport off a DDoS assault, or play out a ransomware assault.
8. Rootkits
A rootkit is altering that gives pernicious entertainers controller of a misfortune’s PC with full real differentiation. Rootkits can be embedded into the application, portion, hypervisor, or firmware. They are spread through phishing, noxious affiliations, undermining downloads, and changed shared drives. Rootkits can in addition be utilized to stow away other malware, like keyloggers.
9. Keylogger
Associations can utilize them to screen specialist improvements and families can utilize them to follow young people’s internet-based lead.
In any case, when introduced for poisonous purposes, keyloggers can be utilized to take secret key information, banking data, and other delicate data. Keyloggers can be embedded into frameworks through phishing, social preparation, or hurtful downloads.

Be the first to comment on "What is different malware?"